Subscriber Benefit
As a subscriber you can listen to articles at work, in the car, or while you work out. Subscribe NowAnthem Inc. spends $50 million a year and employs 200 people to keep its information technology secure.
Yet the Indianapolis-based health insurance giant still left itself vulnerable to hackers on key fronts leading up to the theft of 80 million consumer records, according to details Anthem officials disclosed to their employer clients.
Hackers were able to roam around for seven weeks inside Anthem’s computers before one of the company’s database administrators noticed it on Jan. 27. By then, the hackers had pulled off the third-largest act of corporate cyber espionage in U.S. history, stealing a trove of Social Security numbers, birth dates, email addresses, mailing addresses, and other personal information.
The data breach is particularly ill-timed for Anthem, since it has staked its future on using sophisticated IT to become a trusted guide to consumers as they manage their health and navigate the health care system. While Anthem was well-regarded among health care companies for its IT security practices, the health care industry lags other sectors.
IT security experts say the details disclosed by Anthem show it failed to take three steps that might have stopped the attack—or at least made it more difficult to carry out. The company:
• Didn’t require what’s called “multi-factor authentication” for its entire system. Instead, only parts had the heightened barrier to access, leaving the remainder less protected.
• Didn’t employ monitoring technology that was sufficiently sensitive to detect unusual flows of data out of its computer systems.
• Failed to encrypt the stolen database.
 Anthem did not require its employees to provide two layers of authentication in all areas of its computer systems, according to a Feb. 10 presentation to employers by Tom Miller, Anthem’s chief information officer.
Anthem did not require its employees to provide two layers of authentication in all areas of its computer systems, according to a Feb. 10 presentation to employers by Tom Miller, Anthem’s chief information officer.
The first layer of protection is, of course, a login and password. And the hackers got their hands on the passwords of several of Anthem’s database administrators, according to a Feb. 5 memo Anthem sent to employers.
The second layer is a card, key fob, token or smartphone app that produces a temporary password or a lengthy number, often changing it every hour or even every minute. The computer system produces a matching number at a similar frequency. If someone tries to log in without the matching number for that particular time period, he is denied access. The only way to have the number is to have the card, fob, token or smartphone in one’s hands.
Before the attack, Anthem did not require that second layer in some areas of its IT systems. Almost no company has such a standard for all employees, but it is standard practice for any area in which there is sensitive data.
“Two-factor authentication is not a new or unique concept,” state rules published by the federal Medicare health plan for seniors, which requires it to access sensitive data. “Two-factor authentication is also used every time a bank customer visits the local Automated Teller Machine. One authentication factor is the physical ATM card the customer slides into the ATM. The second factor is the Personal Identification Number they enter.”
Once Anthem discovered the attack, it shut down all IT areas that did not require two-factor authentication.
Then on Feb. 7 and 8, Anthem reworked all its IT accounts that have privileged access to sensitive information to now require three layers of authentication—a permanent login, a physical token, and a temporary password that changes every few hours.
Those were among the “draconian countermeasures” Miller outlined in his Feb. 10 presentation, which he said have been “painful” to Anthem’s business operations.
“I will not accept anyone thinking that this is the result of any kind of sloppiness,” Miller told employers, according to a person who listened to the presentation and took notes. “This is the result of a very sophisticated APT,” he said, using the acronym for advanced persistent threat.
Anthem still does not know the source of the breach, Miller said. Bloomberg News and other media outlets reported that the government and private-sector investigators probing the hack suspect it might have been initiated from China, whose government has been tied recently to numerous hacks of U.S. companies.
IT security experts noted that every major company makes trade-offs between better security and easier use of computer systems by employees and customers.
They also noted that any company can fall victim to a cyber attack—and seven companies with sterling security reputations, such as JPMorgan Chase & Co., have done so recently.
Also, Anthem drew praise for detecting the attack on its own and for quickly alerting the FBI and its customers.
“We believe that Anthem’s adoption of strong information security controls, comprehensive assessment process, participation in cyber preparedness exercises and cyber threat information sharing were crucial in their ability to detect, analyze, remediate and collaborate swiftly and effectively,” stated a Feb. 4 memo from the Health Information Trust Alliance, which coordinates responses to data breaches at health care companies.
‘Pretty shocking’
However, there are technologies Anthem was not using—called user behavior analytics—that could have raised a flag immediately when the patient records were transferred. An Anthem spokesman said the company was using a data loss prevention technology that monitors data traffic on its network, but that it did not detect any suspicious activity.
 Thompson
ThompsonThat’s not surprising, said J.J. Thompson, CEO of Indianapolis-based IT security firm Rook Security.
“There’s a known weakness in that technology,” Thompson said of data loss prevention. Though it’s not common yet in the health care industry, he added, “Our clients are using user behavior anomaly detection tools to identify a pattern of normal behavior and then receive a notice when abnormal behavior takes place.”
Rook Security estimated that a database of 80 million patient records would amount to 35 gigabytes of data.
If it was transferred all at once from the database server to a compromised computer, that much data would certainly have been large enough to attract the attention of user behavior analytics programs, noted Thompson.
If the 80 million records were transferred in smaller chunks, it would have been harder to detect, he said, but there are still things Anthem could have done to make its data traffic monitoring systems more likely to detect unusual transfers.
Rook employees were scheduled to demonstrate on Feb. 13, during the FBI’s National Cybersecurity Summit in Indianapolis, the most likely scenario for how these types of attacks are carried out.
The most plausible scenario, Thompson said, was that the hackers sent a phishing message to Anthem’s IT team. By either opening an attachment or clicking on a Web link in one of the emails, one of Anthem’s own employees could have allowed malicious software to install itself on an Anthem computer.
If opened while an Anthem IT staff member was logged in to the Anthem computer systems—even if logged in via both layers of authentication—such a program could have given the hackers remote access to Anthem’s computers.
Hackers first sent a query—a request for data—to the stolen database on Dec. 10 and continued to do so sporadically until Jan. 27, according to the memo Anthem sent to employers.
 Cate
CateFred Cate, an IT security expert at Indiana University, said that if 80 million records were slowly transferred out of Anthem’s computers, it still should have triggered some sort of notice internally.
“We don’t know the full details of this kind of attack, but the fact that it took seven weeks is going to require some explanation,” Cate said. “It would certainly suggest that the ex-filtration of that data took place over a long period of time. To not notice that is pretty shocking.”
Anthem took flak in various news articles after the attack for not encrypting the database that held the patient records—a practice that has become increasingly common, Cate said.
However, he added, if the hackers obtained the login credentials of IT staff, that would have given them access to the decryption information they needed to read the database.
Anthem CIO Miller, who joined the company last May after more than 30 years at the Coca-Cola Co., told The New York Times after the breach that Anthem had recently been discussing encrypting its sensitive databases and taking other steps to improve IT security—but hadn’t yet.
Thompson said Anthem’s IT security team most likely told Anthem’s executives of the risk of not encrypting, but the executives might not have understood the gravity of the risk they faced.
“Based on the expertise of the Anthem information security team, I find it hard to believe that they weren’t aware of these issues,” Thompson wrote in an email. “I think that the absence of encryption and other critical controls was identified internally and something broke down in communication. This is often the case in internal risk communication and acceptance processes.”
IT security leader
Anthem is recognized for having some of the best IT security in the health care industry.
It has doubled its IT security spending over the past four years. And a recent review by an outside firm of Anthem’s vulnerability to cyber attackers revealed “no significant findings,” according to an Anthem spokesman.
Former Anthem IT workers said the security protocols were more stringent at Anthem than anyplace they’ve worked, including requirements to work with laptops chained to a desk—even while inside Anthem’s offices.
Last April, when Anthem’s corporate name was still WellPoint, the company even set up a website designed to look and feel like its own, at www.we11point.com. It then sent phishing messages to employees to see how they would respond.
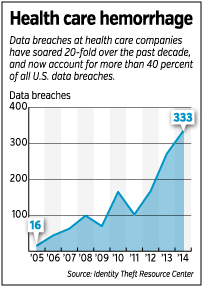
The trouble is, health care organizations are behind other industries when it comes to IT, including security. Cyber thieves have exploited this fact more and more, with the yearly number of health care data breaches in the United States soaring from 16 a decade ago to 333 last year, according to the Identity Theft Resource Center.
“In general, health care has been very slow to adopt almost every technological advance,” said Les Funtleyder, a health care portfolio manager at New York-based E Squared Asset Management. “Right now, a lot of health care companies are sitting ducks.”
Anthem has been investing heavily in IT in a bid to become the trusted mediator of the complicated health care system.
For example, when seven major hospital systems in the Los Angeles area formed a joint venture with Anthem to manage the health of large swaths of patients, they decided to use Anthem’s computer systems to exchange and track patient records.
In addition, Anthem hopes to develop user-friendly websites and mobile applications for consumers, so that it helps them take care of their health—not just process their medical bills.
But Anthem CEO Joe Swedish has acknowledged the company—and the industry—has a ways to go before its computer systems are on par with those of companies like Amazon.com.
 Swedish
Swedish“Health care has simply just not kept pace with our expectations as consumers, and therefore frustration is pre-eminent and growing by virtue of the intolerance of health care’s inability to match the experiences in other aspects of our lives,” Swedish told investors during a January presentation at the J.P. Morgan Healthcare Conference in San Francisco. “We intend to change this dynamic and our strategy is to create an improved customer experience as a distinguishing characteristic of Anthem.”
Major data breaches won’t help any health plan trying this strategy—as most national health plans are—but it will take lots more data breaches before consumers completely lose confidence in health plans, said Dhan Shapurji, a Deloitte consultant to health insurers and hospital systems.
“They clearly are going to be given that opportunity. They have the most data, so it makes the most sense for them to be the consolidator of that [health information],” Shapurji said.
Partly for that reason, Wall Street investors shrugged after the revelation of Anthem’s breach. In the week after the attack was disclosed, Anthem’s share price actually rose 2.8 percent, to $141.49.
Calming customers
In a little more than a year, there have been data breaches at JPMorgan Chase affecting 76 million customers, at Home Depot Inc. affecting 56 million customers, and at Target affecting 70 million customers.
None of those companies has seen their sales affected much, although the CEO of Target was ousted after that breach.
“There’s always a momentary blip, and people are quoted in the newspaper saying they’ll never shop there again, but then they’re back the next time they get a coupon,” Cate said.
Anthem has sought to reassure its customers by paying for two years of identity theft protection and credit monitoring. Sign-ups for that service were scheduled to start Feb. 13.
Anthem also worked to reassure concerned employers, whose workers now could face a lifetime of identity-theft attempts using the stolen information.
That’s why Miller, Anthem’s chief information officer, was conducting town hall meetings with employers.
During the Feb. 10 meeting, one employer even asked Miller if Anthem would share the report being prepared by Mandiant, an IT security firm Anthem hired after the breach was discovered.
“That’s a big request,” Miller said. “We wish to share whatever is necessary to restore confidence, but I don’t know that we would just hand over their report.”•
Please enable JavaScript to view this content.

