Subscriber Benefit
As a subscriber you can listen to articles at work, in the car, or while you work out. Subscribe NowThe wave of computer passwords that has splashed into people’s lives over the last decade has turned into an angry—at times destructive—sea.
Anyone using a computer at work and the internet at home is drowning in the passwords they’re forced to maintain.
And corporate IT departments have become like frantic shipmates aboard a sinking vessel, trying to plug countless holes—often unwittingly created by their co-workers—in their company’s security system.
The stories of wreckage are legendary. Major insurers, national retailers, online corporate behemoths, and mom and pops are among the casualties.
The problem has become so big, many cybersecurity experts think the days of the computer password are numbered. But still others warn that replacing the password with methods such as biometrics—a fingerprint or an eye scan—or multifactor authentication is no panacea.
Much is at stake.
“The damage that can be caused through a breach of someone’s [email or computer system] password is unlimited,” said Fred Cate, an Indiana University law professor and a noted cybersecurity expert. “People can lose their careers. It can be catastrophic.”
And the damage isn’t limited to the person hacked.
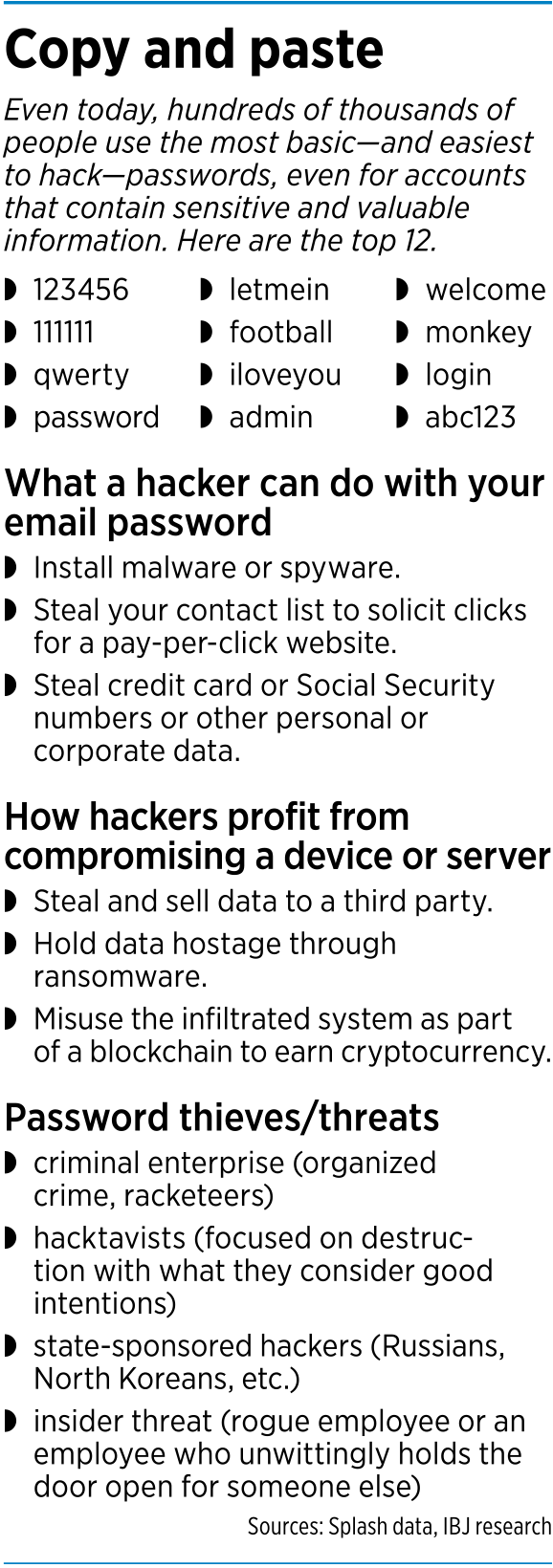
“Ninety percent of successful [cyber] attacks are through fishing or social engineering of an individual in the company,” said Tom Gorup, director of security operations for Carmel-based Rook Security.
Simply gaining access to someone’s corporate email account can cause serious problems.
“Your email is the holy grail. It’s a treasure trove to everything,” Gorup said. “It’s the gateway to getting information on the rest of your life—and oftentimes that of the company that employs you.
 Pelletier
Pelletier“The damage to a company whose employee’s password is hacked can cost a company in the tens of thousands of dollars, but can range into the millions very easily,” Gorup added. “Many companies have 10- to 15-year-old emails stored. So the amount of data that can be compromised is astronomical.”
A hacker with access to an email can quickly reset all the user’s other passwords tracked through the computer system or online—and the original user would have no access to those new passwords.
A hacker can also use the point of entry to deploy a crippling virus or spyware capable of detecting sensitive emails, or to hijack a company’s data servers to demand a cash ransom, or to use its email list to generate clicks for an unrelated website. A savvy hacker can even use a stolen email password to reconfigure a corporate computer system and use it as a cybersecurity mining system.
“Oftentimes, a password is a company’s first and last line of defense,” said Ron Pelletier, founding partner of local cybersecurity firm Pondurance. “And that’s a lot to hang on a simple password.”
 Pushover passwords
Pushover passwords
A major problem—despite the increasing number of horror stories concerning cyberattacks and warnings from IT professionals—is that many people have what cybersecurity professionals call a “weak password.”
“There are a few thousand passwords that would get you into half of all accounts,” said Gene Spafford, a Purdue University professor of computer science and a member of the National Cyber Security Hall of Fame.
Anyone who uses a single word is in imminent danger. A hacker with some chops can use a program to search every single word in the dictionary forward and backward in just a few seconds. Many hackers have programs that can do that in multiple languages, quickly.
Another sure way to escalate the danger of being hacked is to use one of a handful of passwords used by millions of people nationwide. According to multiple sources, the most commonly used passwords include “123456,” “111111,” “password,” “admin,” “login” and “abc123.”
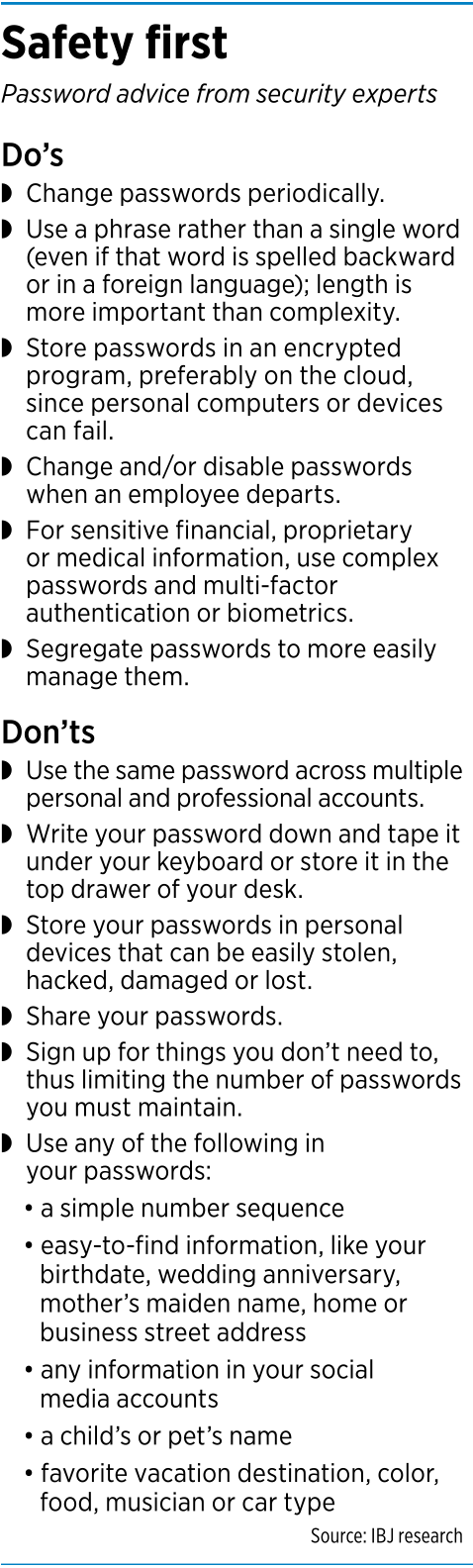
Cybersecurity experts also warn people not to use the same password across multiple accounts—especially if some of those accounts have personal or professional financial data, human resources information or medical information. And never use passwords based on information easily gleaned from your social media accounts or other online footprints.
Gone are the days depicted in the 1983 movie “War Games,” where Stephen Falken, the designer of a computer connected to U.S. nuclear weapons, created a system accessible with the password “Joshua,” the name of his late son.
“You certainly have to construct a wall much higher than that now to keep attacks at bay,” said Cate, a senior fellow of the Center for Applied Cybersecurity Research.
In the mid 2000s, experts began urging people to use arcane passwords with at least one upper-case letter, one lower-case letter, a number and a special character such as an exclamation point or colon. But many people simply used a “1” instead of an “I” or a “$” instead of an “S”.
“It’s amazing how few changes people really made,” said Audrey Taylor, CEO of Netlogx, a local information technology services company that deals with corporate cybersecurity. “It didn’t produce the gobbledygook we had hoped for.”
Phrase, not word
 Cate
CateAnd when people were pushed to create even more complex passwords, they could no longer remember them. As a result, many people began writing them down—in easy-to-find locations.
“Flip over any keyboard or open the top desk drawer at any office, and you often have the password,” Cate said.
In addition, complexity didn’t turn out to be the panacea many computer experts thought. If the password is relatively short, savvy hackers can usually crack it using programs that execute millions of instructions per second.
“Complexity doesn’t matter. It’s length,” Gorup said. “Think passphrase, not password.”
IT experts say it's better if the passphrase doesn't make gramatical sense.And with online activities continuing to increase, the number of passwords people have to maintain is getting unwieldy.
 “People—anyone with a job and any kind of online presence—have dozens of passwords, and it’s going up every year,” Cate said. “With smartphone, tablet and laptop locks, home security systems, and work and home computer applications, it’s not inconceivable for someone to have 50 or more passwords.”
“People—anyone with a job and any kind of online presence—have dozens of passwords, and it’s going up every year,” Cate said. “With smartphone, tablet and laptop locks, home security systems, and work and home computer applications, it’s not inconceivable for someone to have 50 or more passwords.”
Taylor said it’s critical for companies to not only teach employees good “password hygiene,” but to urge them to “take that home with them.”
“Employees are a company’s first line of defense,” she said. “They’re also usually the first point of entry. You have to convince them you’re not doing this to make their lives more difficult. You’re doing this to make their jobs and their systems more secure.”
So what is good password hygiene? Not even cybersecurity experts agree.
While many suggest and many IT administrators mandate changing passwords on all accounts every 30 to 90 days, the National Institute of Standards and Technology recently said that’s unwise because it can become overwhelming for people, causing them to forget their password, get frustrated and possibly return to bad password habits.
Online retailers might not have the luxury of demanding good password hygiene. A third of online shoppers will click away if they are delayed more than five seconds in making a purchase, according to data from Soasta, a company that measures website performance.
“Good security and convenience are always in tension,” Cate said.
Multiple fronts
The email password isn’t the only weak link. Some high-profile corporate infiltrations have come in through passwords to the company’s credit card machine, photocopier and even heating and air-conditioning systems.
“In many cases, those things are all connected to the same system within a company,” Purdue’s Spafford said. “You get in to one of those, and let the fishing expedition begin.”
Corporate officials must carefully track which contractor has which password and change when necessary, Spafford added. The 2014 hack of retail giant Target was infiltrated through credentials given to a vendor working on the heating and air-conditioning system.
Corporate IT staffs are battling the war on multiple fronts.
One mechanism employees are being encouraged to use is cloud-based encrypted storage systems where people can keep their growing list of passwords. Such programs include 1password, Dashlane, Keeper Password Manager and LastPass. Of course, there’s inherent skepticism about storing passwords in a storage unit out of your control.
“The cloud is a scary concept because it sounds like you can just wander around in it,” Netlogx’s Taylor said. “A well-managed cloud, however, has more ability to have the very best supportive technology. Most are highly regulated and highly maintained. They have a recovery system to assure data doesn’t get lost, and the data is not physically in a single location.”
Of course, Taylor added, “not all clouds are created equally.” She warns people to research before they store.
 Taylor
TaylorBut even with managers, passwords remain so problematic, some IT professionals think they need to disappear. Count Taylor among them. “The sooner they’re gone, the better,” she said.
Increasingly, cybersecurity experts prefer biometric devices that use a person’s fingerprint or a retina scan.
Two-fisted defense
Another weapon is what’s called multifactor authentication—a means of requiring at least two independent factors to authenticate a user’s identity when accessing an account. Those factors are often a password and a physical key such as a token or dongle, or a biometric measure.
By law, banks must use multifactor authentication. Some think it’s only a matter of time—as cyber attackers become savvier—before others follow.
“Eventually, the economics will tilt, and we’ll do something more effective than passwords,” Cate said.
Despite their weaknesses, Spafford predicted that “passwords will be around for a while.”
“There are advantages to passwords,” he said. “Passwords are simple, inexpensive and we’re used to them. Users know how to use them and programmers know how to program them. In addition to that, passwords allow people to share access when it’s appropriate and necessary.”
Biometrics can be far more expensive—a single reader can cost $500 or more—and if each device in a company needs a reader, the cost could run into the hundreds of thousands or even millions of dollars for a medium-size or large company.
There’s also a legal upside to having a password.
“If the government wants access, they cannot force you to give up your password,” Cate said. “But [with a warrant], they can press your finger to a device without your consent. So biometrics definitely won’t protect you from government access.”
“Biometrics are going to come, but it’s a significant change, so it won’t be a silver bullet that comes overnight,” Taylor said.
Pondurance’s Pelletier said using multifactor authentication is worth the burden, adding, “It can be applied fairly cheaply with good tools like Google Authenticator or [Google] Duo.”
“Even a small company could do it very cost-effectively,” Pelletier said.
“It comes down to convenience,” he added. “Most companies simply don’t want something that will hurt productivity. But If a password is breached … it could bring a company to its knees.”•
Please enable JavaScript to view this content.
